There are merits to living in a more connected, digital world. With the increase in usage of electronic medical records in hospitals as well as online payment methods and servers that enable an individual to store login information, information storing has become convenient and useful.
This is not an ephemeral trend. Apple has unveiled a feature called “Apple Pay” on the new iPhone 6 that enables users to store credit and debit card information. Gone are the days where data is printed on a sheet of paper and tucked away in a folder.
However, in an increasingly digitized world, crime has become more sophisticated. Just as it is easier for the average resident to store information, it has become easier for cybercriminals to breach data.
In Massachusetts, statistics from the Office of Consumer Affairs and Business Regulation prove that hackers are becoming increasingly adept at stealing personal information and recognizing vulnerability. The hackers have started targeting industries beyond the financial services, probing the education industry.
Personal information in Massachusetts is defined as a person’s first and last name, or first initial and last name, plus any one of the following: social security number, financial account number, a state-issued ID, a driver’s license number or any kind of financial account, said Joanne Campo, deputy general counsel of the Office of Consumer Affairs and Business Regulation.
According to the 2013 Data Privacy Report released by the Office of Consumer Affairs and Business Regulation, in 2013 alone, more than 1.1 million Massachusetts residents were impacted by data breaches, compared to the 340,462 in 2012. Of the 1.1 million residents who had their data compromised, 81 percent of those residents were victims of the Target data breach in December 2013.
“The retail services industry experienced 24 data breaches in 2013, and the significance of the Target data breach is it highlights the enormous impact a single data breach can have on a retailer’s customer base,” Campo said. “It serves as a significant reminder that businesses have to be watchful and vigilant of consumers’ personal information.”
Target is not the only major retailer to suffer a data breach recently. On Sept. 8, Home Depot confirmed a theft at approximately 2,200 of its stores in the United States and Canada, affecting customers who used credit and debit cards in their transactions.
This failure by big businesses to secure their systems is a problem of incentives, said Sharon Goldberg, an assistant professor of computer science at Boston University. Companies devote more time to polishing the surface, the directly consumer-facing side of their business, rather than safeguarding their systems from hackers because the latter is not immediately detectable by the average customer.
“I think what’s maybe less obvious is the fact that usually securing these systems is not the first thing that people think of doing,” she said. “Sometimes we think about getting them working first. So when you log onto a website and it’s slow, you’re going to notice right away. But if you log onto a website and it is unsecure, the average user won’t recognize it.”
In fact, the average user is not vigilant enough, said Quinn Shamblin, executive director of Information Security at BU. The average user looks for convenience.
“People being people, most humans use the same password everywhere or almost everywhere,” Shamblin said. “It is better if you don’t have the same password anywhere.
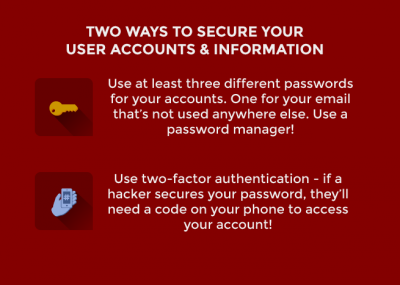
“That was the problem with the Yahoo breach [and] the LinkedIn breach of last year, is that these passwords were stolen and encrypted by the hackers, and most people used that same password everywhere else, and if you use the same password on a hacked site that you use on email, well, we all know that if you want to unlock any online account, go to reset my password, and it will get to your email.”
The 2013 Data Privacy Report found that the education sector experienced exponential growth in data theft, increasing 611 percent from 2012 to 2013. Cybercriminals, tempted by the litany of personal information – such as financial aid and Social Security numbers – found in databases, breached data of 31,870 residents within this sector last year.
“As you can imagine, the education industry has previously been an untapped industry for these cybercriminals, and obviously they’ve determined that it’s right within the information they are interested in – personal information – and they’re going to target it,” Campo said.
The higher education industry has not fully recognized the risks it faces in data security, Shamblin said.
“Higher education [is slower] in understanding that they are at risk [more] than other industries, where it is more obvious,” he said. “If you are in the banking industry, it’s kind of obvious that people are going to come after you because that’s where the money is. And they are typically a bit more sure in security than other organizations. For hackers looking for pockets of opportunity, it’s easier to attack higher [education] because it is a little less secure. They are basically going after low-hanging fruit.”
BU was hit by a phishing incident in December 2013, where emails that asked for passwords were sent to BU employees, and several paychecks were rerouted from employees’ direct deposit accounts. Although hackers attempt to attack BU on a daily basis, Shamblin said, there have been no successful attempts since. In order to further secure the BU system, Shamblin said that the Information Security team is working on a new protocol called two-factor authentication.
“Two-factor authentication means not only you have to use your password, but you also have to have something else, typically your mobile phone,” he said. “When somebody tries to log in to your system and change bank account information now, not only do you have to provide your password, but when they do that, a message goes to your phone, and you get a message saying, ‘Somebody tried to access your account. Is this you?’ And you can verify yes or no. And if it is not you, a report is sent to Information Security so we can try to investigate whether there was a fraudulent access to your account.”
But before this system is implemented at BU, there are several measures students can take to secure their accounts that hold personal information, including password protection.
“I recommend a minimum of three different passwords,” Shamblin said. “One that you use for email and you don’t use it anywhere else, period. Second, the password for your bank and maybe your credit card. And then you have another password that you use for regular sites.”
Shamblin also recommended third-party password managers, which store and memorize your passwords so users don’t have to.
Another precautionary measure is to simply use cash rather than credit or debit cards as a form of payment, Campo suggested. Or, for those who don’t like to carry cash, use a credit card over a debit card.
“They [an individual] could use their credit card while shopping instead of a debit card because a credit card gives the consumer a better chance of finding an unauthorized charge,” she said. “So if the card is compromised, the thieves won’t have direct access to the consumer’s bank account.”